Smart Access, Secure Teams: How Scale’s RBAC and SSO Keep Your Procurement Data Safe
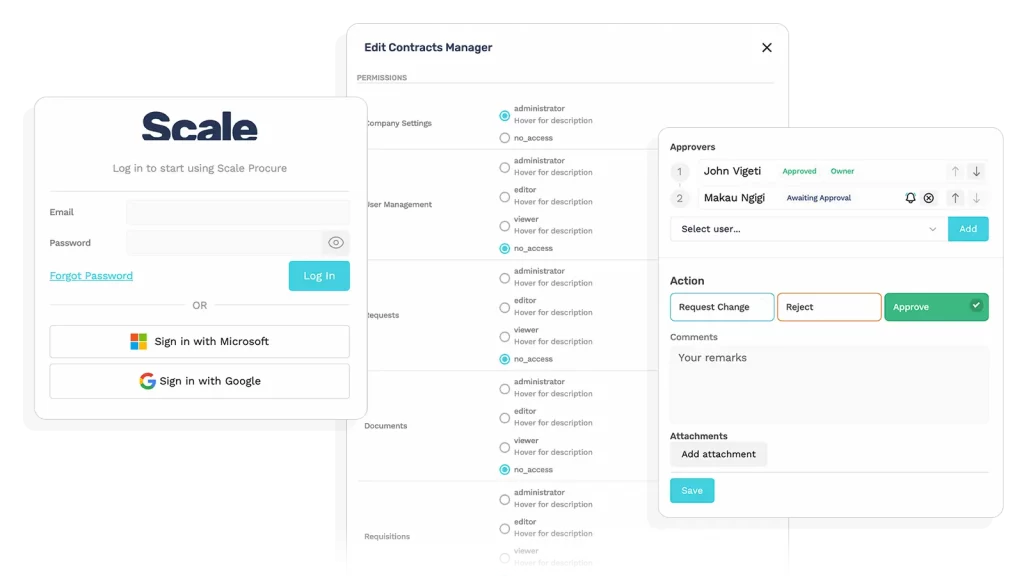
Scale’s Single Sign-On (SSO) allows you to use your company’s credentials to secure access to Scale without needing a new password created.
In any digital landscape today, protecting sensitive information, secure access and maintaining operational clarity is not just good practice, it’s non-negotiable. Whether you’re a procurement head reviewing contract performance or a department user creating a requisition, you should only access what you need – nothing more, nothing less.
That’s where Scale’s Roles-Based Access Control and Permissions module, integrated with Single Sign-On (SSO), steps in as a game-changer.
🔐 Granular Control with Role-Based Permissions
At the core of Scale’s security model is the principle of least privilege: users are granted the minimum access required to perform their roles. This means every action, from viewing supplier profiles to initiating purchase orders, is aligned with clearly defined user roles.
Here’s how it works:
-
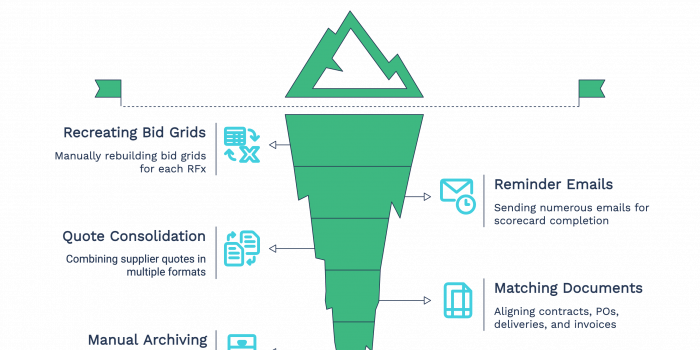
Access Control: Admins can define roles (e.g., Procurement Manager, CFO, CEO, Approver, Evaluator, Finance Officer, Supplier Relationship Manager) and assign specific permissions to each. A user assigned to multiple modules will still only see the modules, data, and documents they are cleared for.
-
Data Security: Sensitive information – like evaluation scorecards, financial documents, or contract terms – is safeguarded from unauthorised users. This reduces the risk of internal data leaks or human error.
-
User-Specific Views: Each user logs in to a tailored interface. Evaluators see submissions and scorecards. Department heads view spend against budget. Suppliers only access the opportunities assigned to them.
-
Activity Monitoring: Every action is tracked – from who uploaded a document to who changed a bid score. This audit trail is essential for compliance, accountability, and performance reviews.
🔑 Seamless Sign-On, Strong Security: SSO Integration
Managing access for large teams can quickly become complex, especially across multiple systems. That’s why Scale integrates with Single Sign-On (SSO) providers, allowing users to authenticate once using their organisation’s credentials and securely access Scale without needing another password.
Benefits include:
-
✅ Fewer Passwords, Less Risk: Reduce phishing and password fatigue.
-
✅ Faster Onboarding: Provision access automatically as team members join or change roles.
-
✅ Enterprise-Grade Authentication: Leverage your existing identity provider (e.g., Azure AD, Okta, Google Workspace) to enforce MFA and login policies.
-
✅ Centralised IT Control: IT admins can revoke or adjust access from one central dashboard without logging into Scale separately.
Together with role-based permissions, SSO ensures access to procurement data is always appropriate, always secure, and always traceable.
🛡️ Compliant by Design: ODPC, Data Controllers & Data Processors
At Scale, we don’t just talk about data protection – we build for it.
As a registered Data Controller and Data Processor under Kenya’s Office of the Data Protection Commissioner (ODPC), Scale is fully compliant with the Data Protection Act, 2019. This means we have legal and operational responsibilities to protect personal and organisational data throughout the procurement process.
Here’s what that means for you:
-
As a Data Controller, Scale determines how and why personal data, such as supplier details or evaluator assignments, is collected and used on our platform.
-
As a Data Processor, we act on behalf of our clients (buyers and suppliers) to securely process this data according to clear instructions and under strict confidentiality.
This dual compliance ensures:
-
Transparent data handling practices
-
Explicit consent and lawful processing of personal data
-
Secure data storage and restricted access
-
Full auditability and accountability
-
Rapid response protocols in case of breaches or data subject requests
📜 We’ve embedded these principles directly into our Role-Based Access and SSO system, ensuring only the right people access sensitive information, and only for the right reasons.
🛡️ Secure Access Without Slowing You Down
Security should never be a roadblock. With Scale, it becomes a silent enabler, allowing each team member to work efficiently, confidently, and securely.
Whether you’re scaling procurement across countries, collaborating with external suppliers, or managing approval workflows, Scale ensures every user sees exactly what they need to and nothing they shouldn’t.
🚀 Ready to Take Control and Secure Access to your Data?
Empower your procurement operations with smart secure access controls, personalised user experiences, and enterprise-level security.
👉 Book a demo today and see how Scale helps you streamline procurement securely.